By default the data that’s sent to and from a Samba share is not encrypted. In this post we’ll enable encryption by changing a few settings in Samba’s configuration file.
This post is part of a series about building a Network-Attached Storage (NAS) with redundancy using a Raspberry Pi (RPi). See here for a list of all posts in this series.
Encryption seems important. If the traffic to and from a Samba share is not encrypted, why do we only talk about encryption now, in some Extras post?
The answer is that for most (home) users enabling encryption in Samba does not add that much security. To the best of my knowledge pretty much all WiFi routers in use today encrypt traffic with WPA2 (or even WPA3) by default1. Unless you shared your WiFi password with your neighbour they won’t be able to decrypt the packages sent on your WiFi2 and so they can’t read your Samba traffic. Your Ethernet traffic is normally not encrypted but typically it’s quite difficult for somebody to gain access to an Ethernet port in your home.
That leaves other users on your network. If somebody on your network has a network sniffer like Wireshark then they will be able to read the data you send to and from the NAS3. In my home network I’m not really worried about that because there are no tech savvy users and I’ve given them access to my shares anyway. However, that might be different in other locations. Also, an additional layer of security is certainly useful. So let’s have a look at encryption.
Check For Encryption
First let’s find out if encryption is used in our current setup. I think the easiest way is to connect to our RPi4 and run sudo smbstatus. This will give an output similar to the one below.
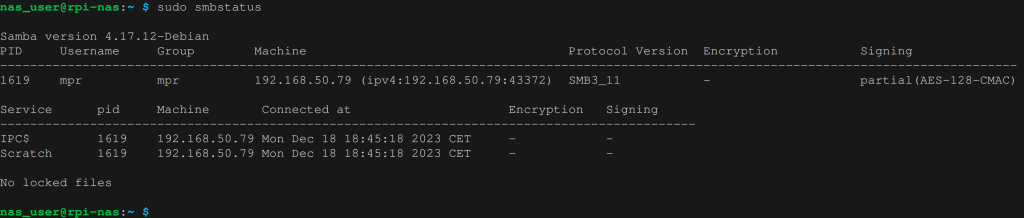
That output tells us that we’re using SMB version 3.1.1. but that the share Scratch is not encrypted (there’s a dash ‘-‘ underneath encryption).
Alternatively, we can also use Wireshark5 (that takes a bit more effort but I find it very satisfying). After you open the program select your network interface, in my case that’s wlan0.
Wireshark will capture all sorts of packets. We only want to monitor those that use the Samba protocol and that go to our NAS, so we can filter as shown below (replace the IP address with the one of your RPi).
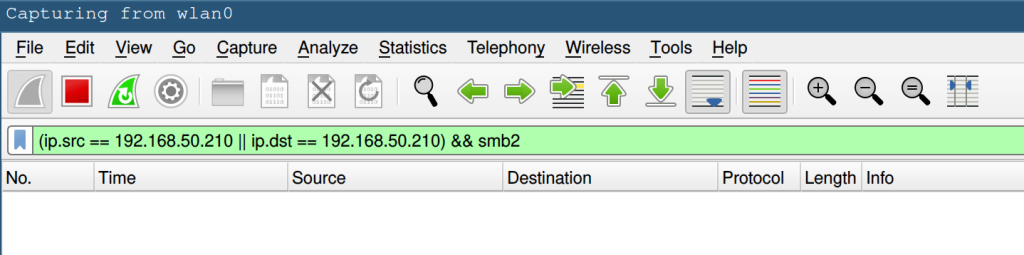
To test if the connection is encrypted we can, for example, read some file on a mounted share with cat /path/to/share/somefile. Then we look at the packets in Wireshark and try to find the contents of somefile.
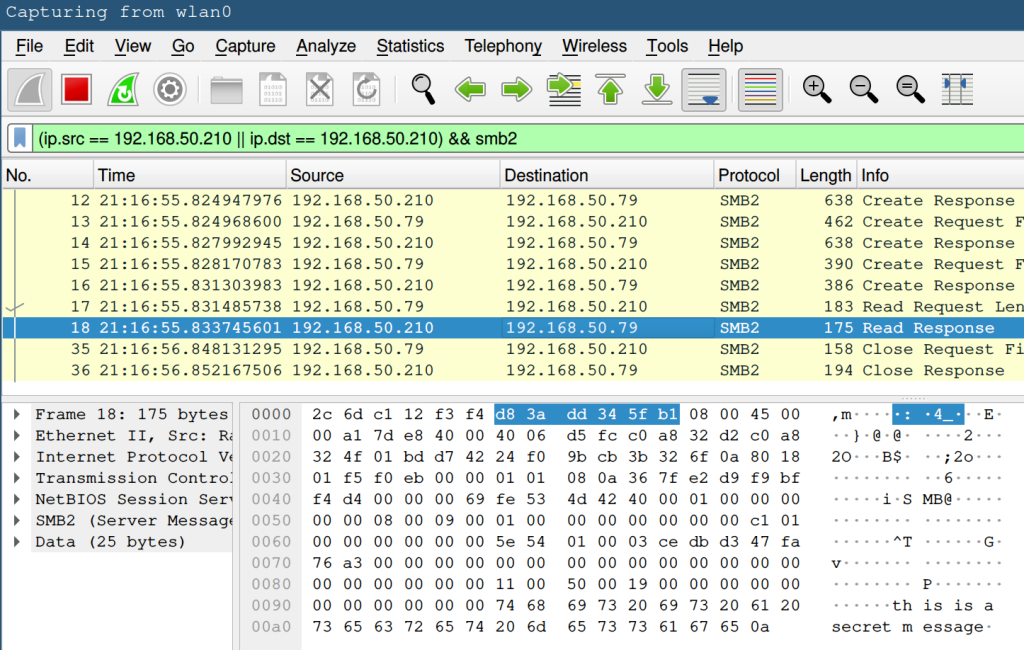
If you look at the bottom right of the screenshot you’ll see “this is a secret message” in plain text. That corresponds exactly to the contents of somefile so the Samba connection is not encrypted.
You may be wondering why we can read the packets even though we’re using encrypted WiFi. That’s because by the time Wireshark gets the packets they have already been decrypted by our computer. So WiFi encryption won’t show up when we use Wireshark in this way6.
Enabling Encryption
To enable encryption, connect to your Raspberry Pi and open the Samba configuration file.
sudo vim /etc/samba/smb.confIn that file, under [global], add the following line.
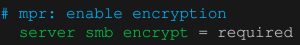
This line forces the connection to be encrypted. If a client is not capable of encryption then it won’t be able to connect to the NAS (to my knowledge all modern computers should be able to use encryption).
FYI, if you look at the man pages of smb.conf 7 then you’ll find that the effect of this option depends on the Samba version that’s being used. Version 1 didn’t have any native Samba encryption. Instead it used Unix extensions (which we have to disable due to the way Greyhole is implemented). However, version 1 has been deprecated and only clients that support at least version 2, which supports native encryption, can connect (see option min protocol).
So after we close the file we restart the Samba daemon.
sudo systemctl restart smbdIf we run sudo smbstatus again we’ll see that the connection is now encrypted,
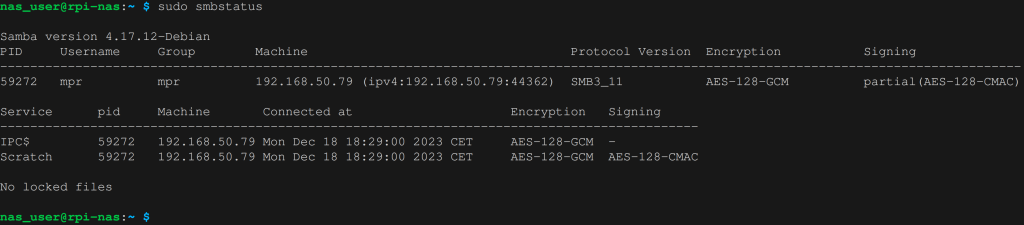
and the packets captured by Wireshark are unreadable.
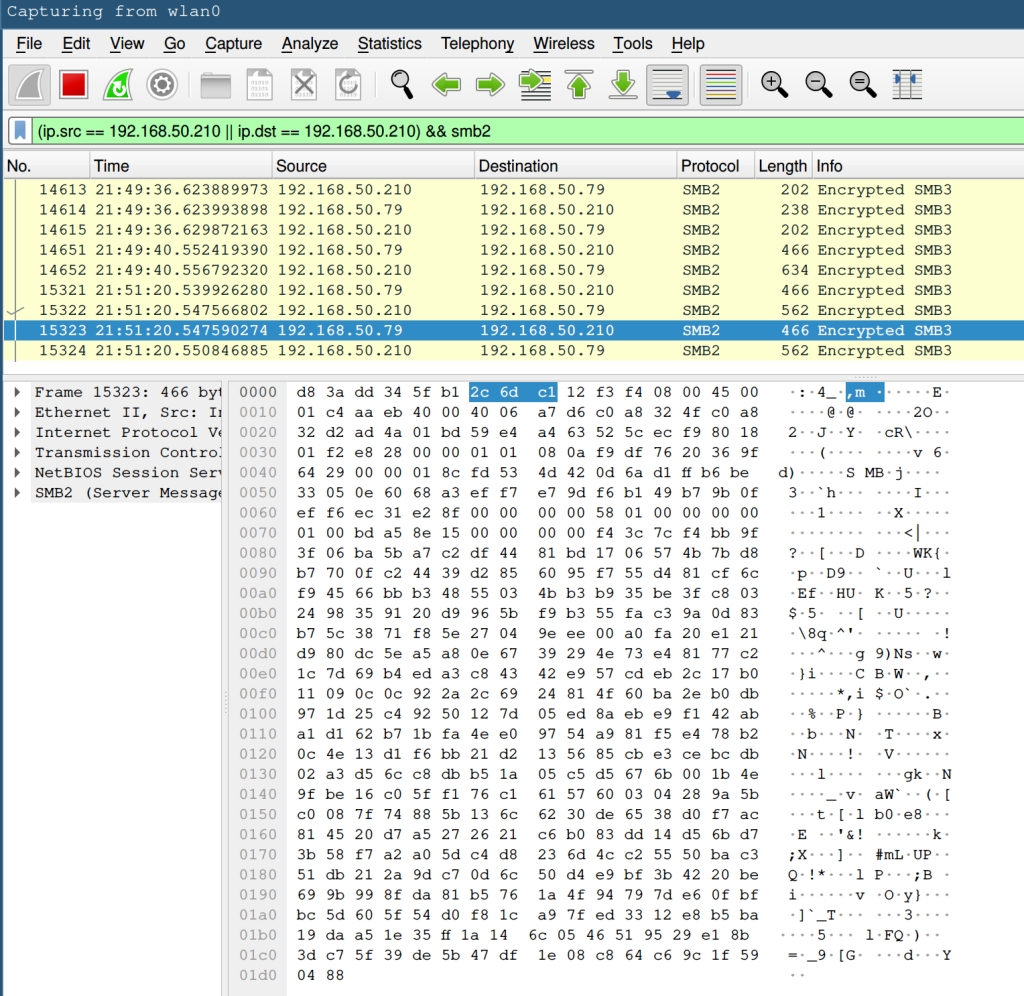
So that’s it. We’ve now got an extra layer of security for our Samba connections.
Footnotes:
- At least that’s what I see when I look at the WiFi networks around me. ↩︎
- The chances of somebody breaking WPA2 encryption are rather slim. ↩︎
- Maybe more importantly, if they are in the same household as you then they probably have physical access to the NAS. Since we haven’t encrypted the drives anybody could just take them, mount them on their computer and read all the data. ↩︎
- With SSH or directly connecting the RPi to a screen, either way will be fine. ↩︎
- There are quite a few websites showing you how to install and set up Wireshark. If you don’t see a network adapter then you may have to add your user to the network group with sudo usermod -a -G network username. ↩︎
- We’re only monitoring the traffic of our own computer here. You can also use Wireshark to monitor traffic that’s not addressed to our computer. If you know the WiFi password of the connection you’re monitoring then you can decrypt those packages, otherwise they will all be encrypted. ↩︎
- You can open them from the terminal with
man smb.conf. ↩︎
Leave a Reply